After sleeping this morning, everyone in the group was discussing the carnival brought by the NBA to scientists last night. It is said that someone directly free Mint 100. According to the current price of 0.4eth, it is also 150000 US dollars. The reason is that there are loopholes in the contract, so let's see what's going on.
The NBA released its NFT series the association NFT yesterday. It produced 75 NFTs for 240 players, with a total supply of 18000. White list holders can have one free mint. The key point of this sentence is to circle. The article on gh0stlygh0sts mentioned earlier is also free mint. You can sit and wait for appreciation only by paying gas fees. If you can find some contract loopholes in the visible profit space, For example, if you bypass the white list or the limit of Mint 1, you can't make enough money. Therefore, whenever such NFT projects appear, a large number of scientists will stare at looking for loopholes. This time, the NBA blew up the king, and both the white list limit and the limit of mint 1 were broken.
This vulnerability is also a great blow to the hard-working users of the white list. Even if people without the white list can mint, they can mint indefinitely, resulting in robbing the number of users with the white list. Even many users spent thousands of dollars on the white list off-site. In addition, a large number of scientists poured in during the mint, which led to the surge of gas fees, and the white list users were forced to pay more gas (after all, one of the purposes of the white list is to avoid gas war). Therefore, a large number of users were crying for their rights, and the white list users were crying in DC.
This problem is mainly caused by two situations:
1. Users bypass the official website and directly interact with the contract through matemask with the hexadecimal input data generated by others.
2. There are loopholes in the contract for the white list verification of mint.
Let's talk about the first one first. Let's test your knowledge. What are the ways to interact with smart contracts in mint?
First of all, you will definitely say, don't you click a "MINT" button on the website to call the smart contract to mint?
This is the most routine operation that all project parties hope we can carry out. Everyone should have the experience of squatting in front of the screen and poking the mint button to grab the public sale.
In addition, experienced students will say that they can also directly open blockchain browsers such as Etherscan, find the contract address of the project party, and operate the contract in read contract and write contract. Many students grab the public sale in this way, because you click mint on the official website, the front end will trigger a request to operate the contract, and the contract will be executed again. If you operate the contract directly in Etherscan, you will skip the first step, The speed is faster. For those who don't understand this method, you can see my previous article how to understand the NFT project by reading Etherscan?
However, this method will not work in two cases. One is that the project party does not open source its contract at all, or the project party must require you to pass in some parameters such as signature in the contract interface, and this parameter can only be generated through the centralized server of the project party, so you are forced to operate through the official website of the project party.
In fact, there is a third kind, which operates directly with the contract through matemask wallet.
You may be very unfamiliar with this kind of operation. In fact, you have unconsciously used this operation in a large number. The process of transfer is actually the process of directly exchanging contracts with your wallet.
When I transfer money to an address, first click send.
Then enter the collection address and enter the amount you want to transfer.
You are already familiar with this process. In fact, this is the process of your interaction with the contract, because the action of transfer is that I transfer the money to an address. The address only needs to collect the money, and there is no need for me to enter more additional information. At this time, you will ask, mint is different. At least I need to enter several mint, including white list verification. How to enter these parameters?
We open the settings of metamask wallet, enter advanced, and then pull down to see a switch called "display hexadecimal data", turn it on.
What is this switch for? We need to clarify what hexadecimal data is for you first.
When you interact with any contract, you will input certain data for it. The contract receives this part of data for processing. This data defines which interface function you want to interact with, what parameters you want to pass to this interface function, etc. These data will be compressed in the form of 16 process.
You can open Etherscan, find a transaction record you once had at random, click to enter the details, and then keep pulling down. You will see input data at the bottom, with a long string of characters on the right, which is what the data you entered when interacting with the function of this contract will look like after it is converted into hexadecimal.
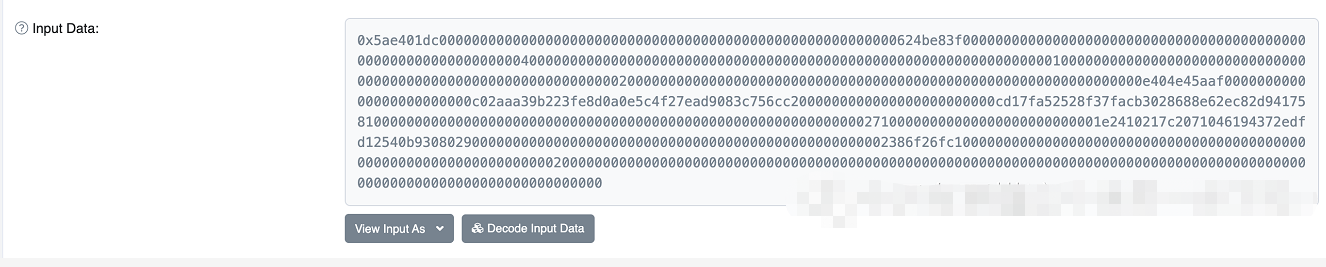
The key is that this long string of irregular numbers don't understand at all. Don't worry first. There are rules in it. Although this NBA loophole doesn't require you to read hexadecimal, you can use it directly, but with a realistic attitude, we still need to be able to understand the meaning.
First, we can see that there are several characters after the first 0x, and then all 0.
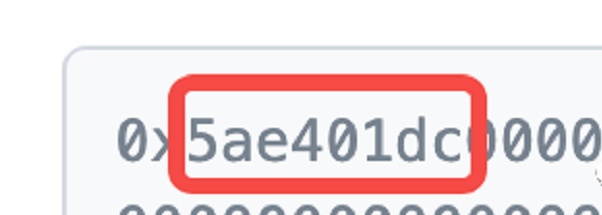
These characters represent the code of the contract function you call, and each function will have its own code.
When we open the transaction record of a contract, you will see that some of the methods called are understandable words such as mint and transfer, and some are codes beginning with 0x. Because the operation functions such as mint and transfer are very standard, Etherscan automatically helps you translate their codes into words, but some functions are developed by the project party, so only their original codes are displayed.
Let's try the process of directly interacting with the contract in this way in the test network. I found a set of contracts deployed before, and then click to enter the details of the completed Mint transaction.
Then pull to the bottom and copy the input data at that time.
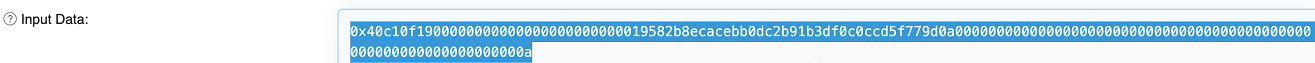
After filling in the address of the contract just now, click data to enter the next.
Then it comes to the step of paying gas fee.
We can click the data to have a look. Sure enough, the function type here is mint. Yes, it is the mint function, which shows that we have successfully called the contract with the previous hexadecimal input data.
Then click to confirm the payment of gas fee. Go to Etherscan and have a look. It's successful!
Well, by now, we have clearly known that the contract function can be executed once with the hexadecimal data of existing transactions.
We just talked about the reasons for this problem. The second point is that there are loopholes in the contract verification white list. This loophole gives scientists the opportunity to collect it by hexadecimal means.
Next, let's look at what's wrong with the contract mint. Readers who have read my previous articles should know that there are several levels of verification during mint, mainly including whether to enable Mint verification, quantity verification and white list verification. As shown in the NBA Mint contract below, it has three levels of verification:
Batchnumber is used to verify the batch of mints. This is not the focus of our discussion today. We can skip it first.
The focus is on the white list verification of the second layer and the mint quantity verification of the third layer.
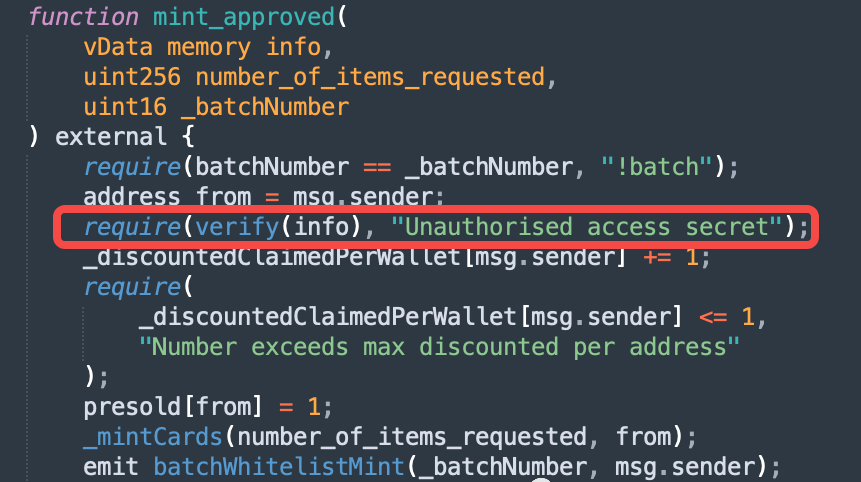
Here's the point. The second level verification uses a function called verify, which passes in an info parameter, which is used to verify whether the current user is on the white list. That's the problem.
Before explaining the problem of whitelist verification, it is necessary for us to first understand the two common whitelist verification methods. In the early stage of NFT industry, the whitelists of many projects were entered one by one, and then check whether the current user's address can match the whitelist in mint. Each entry requires a gas fee, which is very expensive, Someone around me spent tens of thousands of dollars just entering the white list.
Gradually, some people realized that this method is expensive and stupid, so they adopted a method with higher technical difficulty but more saving gas cost, such as the encrypted signature verification of Merkel tree. Its principle is to put the white list under the chain instead of being stored in the contract on the chain, which is kept by the project party. When the user is on the official website mint, a signature is generated by algorithm according to the user's wallet address, The NBA uses the verification of encrypted signature this time.
The specific encryption principle and code implementation are too complex. Skip it first. Those interested can learn elliptic encryption algorithm and Merkel tree by themselves. Let's understand the principle first. Now we only need to know that the verification method is to enter a wallet address, verify whether the address exists in the white list, and return a signature if it exists.
At this time, you may feel that there is a problem. Since the verification method is to enter the address and return the result, if I use the hexadecimal interaction method just mentioned, I can enter the transaction hexadecimal data executed by the white list user, can I complete the "white list MINT", which is equivalent to opening the door for fingerprint identification. You can also enter the door by cutting off the fingers of the authorized person and putting them on the identification machine.
The problem here is that if the project side adds another layer of verification, for example, the mint address and the verification whitelist address must be the same, that is, the finger you unlock and the person who enters the door must be integrated. This loophole will be blocked, but the NBA has not been blocked yet.
Let's review the code, first with MSG Sender obtains the user address of the current contract execution, which is passed in when Mint is finally executed.
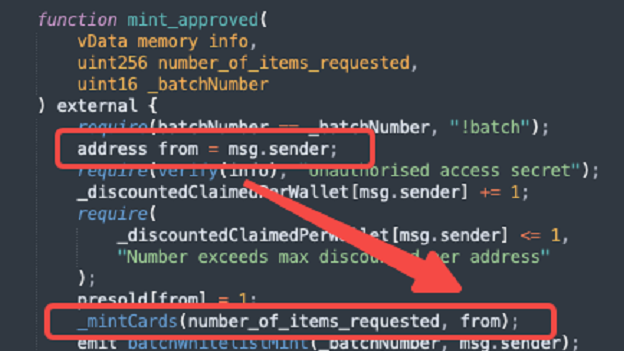
The verification before Mint is to pass in a parameter called info. The address contained in the parameter info is passed in after the official website obtains the address of the user operating the official website.
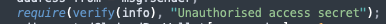
Do you understand the problem? A with a white list clicks mint on the official website. The official website passes the contract verification after passing the address of a into info. Then, when the contract executes Mint again, get the address of a currently executing and transfer the NFT to him, but! But I didn't judge whether it was the same person! He didn't check whether the two addresses were the same.
So I can find a's transaction record first, and then copy and paste his hexadecimal into my wallet to execute the transaction. At this time, I use a's address when verifying the white list, so I will pass the verification, but I use my address when mint, because I am interacting with the contract.
Solved the case! Fine or not! I cut off a's finger and went into the vault!
Let's take a look at the hexadecimal length of users who use the white list mint. We can see that he Mint an NFT in this address and succeeded.
Then let's look at hexadecimal. There are two key points. The number 1 represents his mint. The following address is his own address. Right.
Let's take a look at what a giant who rolled 69 in the circle of scientists did yesterday. Here are his address and 100 NFTs of mint.
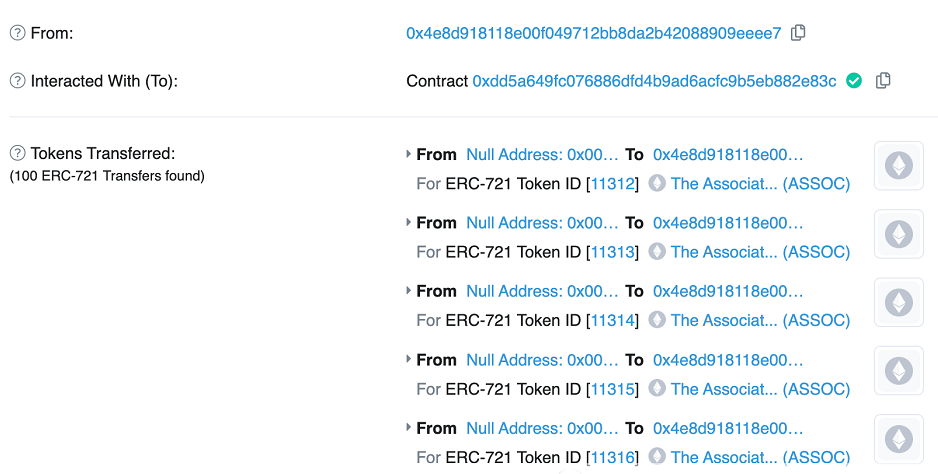
Let's take a look at what his hexadecimal is. Let's see 45 first. What does that mean? Doesn't that mean quantity? It's neither 1 nor 64, because when hexadecimal 45 is changed to hexadecimal, it's 69, so this person changes 1 to 45 and gets 69.

Don't you think there's a limit of one per person? Here is another vulnerability. We see that the code does have a limit. When mint, your holding can't exceed 1, but when I mint, it's 0. I Mint 10000. This limit can't control me I don't know what the contract engineer is thinking.
Next, let's go back to the hexadecimal data and look at the contract address. You'll find that it doesn't match this person. It means that this person cut off his finger and unlocked it. Let's see which unlucky guy it is.
Enter his address and see that the boy is also very rich. There are 30 ethers lying on the account. It's not a loss to be robbed.
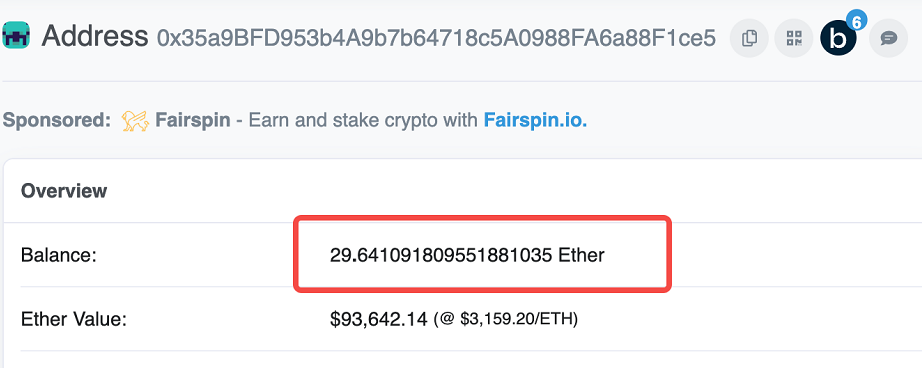
Then I saw that his trading record did Mint an NBA last night. It seems that this man unlocked the lock with his hexadecimal.